Very simply, cryptojacking is the illicit use of third-party devices such as laptops, tablets, or smartphones to secretly mine cryptocurrency without the knowledge or consent of the device’s owners. This type of hack steals a portion of your computer’s resources and dedicates it to solving cryptographic puzzles on the hacker’s behalf. 2022 saw a 230 percent increase in cryptojacking malware, with 215,843 infections on various devices.
As a victim of cryptojacking, you’ll be saddled with all the costs, such as high electricity bills and inefficient system performance, without reaping any rewards. Ultimately, it’s a situation that you would rather avoid.
Cryptojacking software is designed to be subtle so that users don’t notice something’s amiss. After all, most of us won’t constantly check system performance and examine the processes in our system tray. If our devices perform slower than usual, we often blame the latest software update or the dozens of tabs opened on our browsers. Likewise, if our cooling fan turns on more often than before, we assume our device needs to be upgraded or serviced.
However, these subtle signs may indicate the presence of cryptojacking software.
How does cryptojacking work?
Cryptojacking works by hijacking access privileges on devices and then using those privileges to implant mining malware. The malware then steals the device’s CPU resources to mine crypto for the cryptojacker. From browser scripts to malicious links, there are a number of ways that cryptojacking malware can appear on your device:
Browser cryptojacking
In this case, cryptojackers embed a specific code onto websites and take advantage of the computing capacity of unsuspecting website visitors.
This form of browser cryptojacking peaked from 2017 to 2019, with hackers using the Coinhive web service to hijack and monetize web browsers. However, browser cryptojacking became unprofitable once browser makers started developing security measures and hackers have largely moved on to more lucrative methods.
While browser cryptojacking has waned, insecure browsers can still be targets. To prevent cryptojacking and other browser-based attacks, be careful of the websites you visit and the sort of permissions you grant these sites
In-host cryptojacking
In a method similar to phishing and malware attacks, the cryptojacker sends a harmless-looking link that automatically installs cryptomining software onto a victim’s device (also known as the “host”).
This sort of cryptojacking can also occur when cryptojackers include links and mining software in an app’s installation package. For example, if a user downloads popular software like Adobe Photoshop through third-party sites, a cryptojacker might add mining software to the package before making it available for download.
Taking control of network infrastructure
Here, cryptojackers who are also experienced hackers gain unauthorized access into their victim’s ecosystem of devices undetected. In this instance, a cryptojacker can hack into a victim’s Wi-Fi router to get access to their desktop, phone, and any other devices, install mining software and use that to mine crypto.
Using cloud services
Through this method, cryptojackers use rented cloud computer software (paid for by their victims) to mine crypto. This method is popular because miners don’t have to install any software on their devices, and they can participate in mining remotely. There are two ways that cloud services can be highjacked: they can compromise specific virtual servers and install malware directly onto them, or they can compromise a cloud account and create new cloud instances for mining cryptocurrencies.
How do I detect cryptojacking?
It’s relatively easy to determine if you’ve fallen victim to cryptojacking. Below, we share some tell-tale signs:
Suspiciously high electricity bills
Right off the bat, the first thing that tells someone that they’re a victim of cryptojacking are high electricity bills. In 2022, it takes about 1,449 kilowatt hours (kWh) to mine a single Bitcoin. With the average cost of one kWh in the U.S. being about 21 cents, this equates to about 30,429 USD in electricity bills.
It’s also worth noting that the price of a cryptocurrency determines its value and, in turn, the amount of energy it takes to mine one coin. Of course, this also depends on where you are and the electricity cost in your location.
Overheating
As we know, crypto mining requires a lot of processing power which could lead to overheating of your devices. If you notice that your phone, laptop, or other hardware is heating up even if you’ve not been actively using it, your device might be affected by crypto-mining software.
Poor performance
Because crypto mining takes up a lot of bandwidth and processing power on devices, it might lead to poorer performance on other apps. If you notice that your phone or laptop has been lagging lately, there’s a likelihood that your device has been compromised.
High central processing unit (CPU) usage
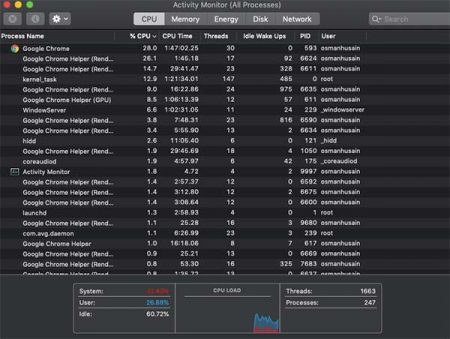
If you feel that you have fallen victim to a cryptojacking scheme, the first thing you should do is check CPU usage. Your CPU usage will show you if any app or software is using an unusually high amount of processing power.
For Mac users, simply navigate to Launchpad > Activity Monitor > CPU.
For Windows users, open up Task Manager > Processes > CPU.
A CPU running at normal levels should look something like this:
![]()
If your system utilization is at a high percentage, despite minimal use of processes and apps, you may have fallen victim to a cryptojacking scheme.
How to prevent cryptojacking?
Malicious programs designed to covertly mine cryptocurrencies on your device spread like any other virus or malware. Hence, guarding against them requires attention to better cybersecurity hygiene.
Protect your router
Your router is the gateway to your entire network, making it the most important thing to protect. One basic cybersecurity tip is to change your router’s default password. This prevents hackers from easily guessing your password and controlling your network.
Another important way to protect your network is to enable firewalls on your Wi-Fi network. A firewall can help block and monitor unauthorized incoming and outgoing traffic and prevent suspicious activity from malicious parties.
Use ad blocker and disable javascript
In 2021, hackers were able to slip crypto mining codes onto third-party ads. The Javascript-enabled ad tricked page viewers into clicking a pop-up ad that, when interacted with, started the mining process.
To protect yourself from becoming an unsuspecting victim of a cryptojacking app, download and enable an ad blocker on your devices.
You might also want to go one step further and disable Javascript on your browser. To disable Javascript on Chrome, here’s what to do:
- Click on the three vertical dots at the top-right corner of the window
![]()
2. Select Settings
![]()
3. Navigate to Privacy and Security and select Site Settings
![]()
4. Look for Permissions and toggle JavaScript settings
![]()
Secure servers and cloud configurations
Cryptojacking could slow down or even crash cloud servers, resulting in productivity loss and other issues. As the subscriber of the cloud service, you might also incur additional costs for the increased amount of processing power and server memory.
A great way to secure and monitor cloud configurations is to use security solutions such as Cloud Access Security Brokers (CASB) that can monitor and control access to cloud services and data and can detect and prevent cloud-based cryptojacking attempts.
Use software composition analysis (SCA)
SCA is an automated process that identifies any known vulnerabilities or license compliance issues in the codes of open-source software. The SCA ensures that the software is secure and compliant with industry standards. With SCA, you’ll be able to determine if software you’ve downloaded has any line of crypto mining code.
Block infected sites
While there isn’t a full list of websites that have been compromised by cryptojacking software, companies like Microsoft and MalwareBytes maintain a list of malware-infected sites and various known viruses that serve as great resources for internet users.
You can use these lists to create a block list of your own. In addition, it might also be wise to stay up to date on cybersecurity news about new types of malware and viruses.
Avoid clicking on unusual links
Clicking on unusual links can put your computer and personal information at risk. Unusual links are often used in phishing scams, which are attempts to trick you into revealing sensitive information such as passwords or credit card numbers. Some links can also lead to cryptojacking malware, too.
Keep all devices and software up to date
It’s also essential to keep your devices updated at all times (we recommend turning on automatic updates) and only install software or apps from official marketplaces.
Install anti-cryptojacking browser extensions
Some browser add-ons claim to guard against cryptocurrency mining. For starters, the Opera browser has an in-built protection that guards against this threat, akin to ad-blockers on web pages.
If you prefer to stick with Chrome, you can download the No Coin extension, while Firefox users can utilize the NoMiner add-on.
If you own a company, instruct your IT team and educate your employees
To protect your company’s resources and your employees from cryptojacking malware, it’s important to set clear policies on cryptomining and guidelines for the personal use of company resources like internet bandwidth and cloud servers.
In addition to this, you might also want to set up relevant training sessions on how to identify and prevent cryptojacking, including how to spot signs of a cryptojacking infection and how to use security tools to detect and remove malware.
Common cryptojacking attack methods
Endpoint attacks
In cryptojacking, endpoint attacks occur when a device connected to a network is infected with malware to mine cryptocurrency. Devices can be infected by malware when a user clicks a phishing email, download infected software, or after hackers have exploited vulnerabilities in the device’s operating system or software.
Scan for vulnerable servers and network devices
Cryptojackers often use open-sourced vulnerability and network scanners to determine if a device or network has vulnerabilities that could be exploited. Once a device has been compromised, the attacker will install cryptojacking malware and use its resources to mine.
Leveraging cloud infrastructure
Cryptojackers leverage cloud infrastructure by using the cloud resources of a victim, such as virtual machines or Docker containers, to mine cryptocurrency without their knowledge or consent. To do this, cryptojackers will look for vulnerabilities in a user’s cloud infrastructure or steal their login credentials to access their account.
Is cryptojacking widespread?
The amount of cryptocurrency that can be mined from a single device is rather minuscule, but when cryptojacking software reaches hundreds of thousands of devices, it becomes very lucrative. Plus, it entails zero cost for the hacker.
That’s precisely why cryptojacking is far more common than you might think. The Federal Trade Commission warns against it, urging users to be mindful of “scammers using your computer as their virtual ATM.” In 2017, Fortune declared cryptojacking the “next big cybersecurity threat.” Even Cristiano Ronaldo’s official website has fallen victim to cryptojacking, with dubious code capable of mining Monero surfacing a couple of years ago.
In their 2022 report, cybersecurity firm SonicWall suspects that the rise in cryptojacking cases is due in part to the fact that governments worldwide are cracking down on ransomware attacks, causing experienced cybercriminals to have to switch tactics.
Cryptojacking isn’t likely to magically disappear anytime soon, and hackers may come up with even more ingenious methods to extract our system resources for their benefit. However, as long as you remain cautious and alert, you can avoid becoming a cryptojacking victim.
On the flip side, if you want to share some of your excess computing resources to help a good cause, check out Donate Your Tab.
FAQ: About cryptojacking
Whether cryptojacking is legal or illegal depends entirely on the situation. For example, if a cryptojacker has hacked into a user’s hardware or cloud infrastructure without their knowledge, cryptojacking in this case would be considered illegal. However, if a user or even a company has permitted a cryptojacker to use their device or resources for mining crypto, then, cryptojacking in this instance is not considered illegal.
Cryptojacking scripts are lines of code (commonly Javascript) that are designed to mine crypto. These scripts can be embedded into websites and advertisements, and then delivered through malicious email attachments.
Cryptojacking occurs because mining crypto is a profitable activity. However, mining crypto uses a large amount of computational power, energy, and equipment, which can be costly. Thus, cryptojackers use the resources of other people to save costs on mining and earn a higher profit.
Some antivirus software can detect malicious scripts used for cryptojacking. However, new types of cryptojacking scripts and software are constantly being developed to evade detection. As such, you should always keep your antivirus software updated.
There are various ways that cryptojackers find their victims so that they can use their computing resources for cryptomining. One way cryptojackers look for victims is through compromised databases that hold software and hardware information.
For example, suppose customer information from a hardware producer like HP or Apple gets leaked. In that case, cryptojackers will know what sort of hardware their customers are using and the sort of processing power each device has.
The term “cryptocurrency,” a combination of “cryptography” and “currency,” alludes to the fact that cryptocurrencies are a form of digital money that uses cryptographic keys to identify its account holders and signatures to authenticate transactions. Cryptocurrencies only enter circulation through “mining,” a process used both to create new units of currency and secure the ledger from tampering.
The mining process typically involves powerful, high-performance computers, which miners use to compete with one another to reap rewards. Before cryptocurrencies became as popular as they are today, it was possible to mine them with regular computers. However, cryptocurrencies such as Bitcoin are typically mined in extensive farms that feature hundreds of computers working in unison and around the clock.