What line of defense do you have against malicious traffic and software? Do you have a firewall protecting your infrastructure?
Security is at the forefront of the technology discussion. As the industry innovates and builds websites, applications, and platforms, securing the environments where these things live is increasingly essential.
In the web hosting space, there are many options for securing your infrastructure. But how do you know which security options to choose?
A firewall can prove to be a simple, effective, and modest solution for data security.
What is a Firewall?
A firewall is a device used in network security to monitor incoming and outgoing network traffic and determine whether to allow or block it based on a predetermined set of security rules. You can refuse access to unauthorized traffic while legitimate traffic can be allowed to reach its destination. Firewalls also block malicious software from infecting your computer.
What is the Purpose of a Firewall?

The purpose of a firewall is to reduce or eliminate unwanted network connections and increase the free flow of legitimate traffic. Firewalls are an essential addition to your infrastructure because they can help isolate computers and servers from the Internet to provide security and privacy of data. As previously mentioned, not only do they monitor traffic to and from your server, but they limit that traffic in some cases as well.
For example, if we think about a Denial of Service (DoS) attack, erroneous traffic floods your site and can potentially bring down the targeted website’s server. Appropriately configured firewalls can help protect your environment from such situations. You can filter traffic and search patterns for anomalies that point to an attack being underway.
How Do Firewalls Work?
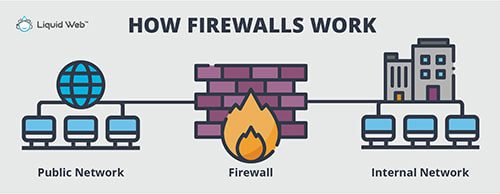
A firewall monitors all data traffic to allow good data and block bad data based on preset rules. It uses one or any combination of three methods: Packet Filtering, Stateful Inspection, and Proxy Service.
- The Packet Filtering method gets implemented to monitor network connectivity. Data packets are units of data packaged together that travel along a given network path. The packages are analyzed and compared against the configuration rules or “access-list.” The firewall then determines what is allowed or denied access to your environment.
- Stateful Inspection method allows the analysis of traffic flow patterns according to state, port, and protocol. The firewall monitors activity on a connection from open to close. It keeps track of known, trusted packets to determine authorized data from the website or application versus any data from hackers or other website security breaches.
- The Proxy Service method prevents direct network connections between Internet traffic and the server. This type of implementation takes stateful inspection a step further. The firewall acts as an intermediary between your server and the requests made by the end user. Entire data packets are examined and either blocked or allowed based on the rules set.
Is a Firewall a Type of Software?
Firewalls can be software-based or hardware-based. Each type of firewall has its unique pros and cons. However, the primary goal of a firewall is to block malicious traffic requests and data packets while allowing legitimate traffic through.
Both hardware and software firewalls help to monitor and filter incoming and outgoing network traffic based on previously established security policies. In other words, a firewall determines whether to allow or block the network traffic based on a predetermined set of security rules.
What is the Difference Between a Hardware vs Software Firewall?
The key difference between a hardware firewall and a software firewall is that a hardware firewall runs on its physical device, while a software firewall is installed on one or more machines.
What is a Hardware Firewall?
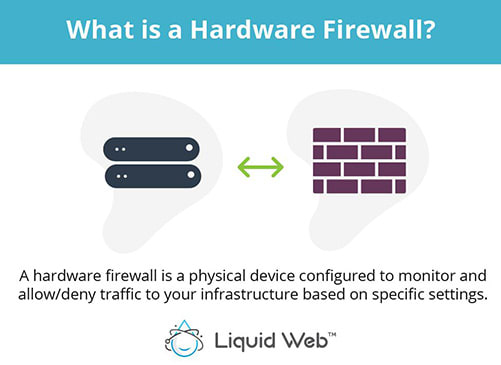
A hardware firewall is a physical device configured to monitor and allow/deny traffic to your infrastructure based on specific settings. A hardware firewall also allows for the highest performance on your servers by keeping the firewall separate from your server, thereby not using any server resources.
Having a hardware firewall ensures you have 100 percent control of the traffic on your network. With a single device, you can decide what traffic should or should not reach your servers. There is no need to install or enable software firewalls as packets are to be intercepted and analyzed before reaching your servers.
Hardware firewalls are also easily configured. There are usually default rules you can set and apply to all traffic. Granular control to drill rules down to distinct ports and services like SSH (Secure Shell) and RDP (Remote Desktop Protocol) makes fine-tuning simple.
Another benefit to hardware firewalls is the ability to set up a Virtual Private Network (VPN) connection directly to your environment. Wherever there is a stable Internet connection, you can access your infrastructure.
What is a Software Firewall?

A software firewall is a firewall installed on your local computer that allows or denies traffic to and from your computer based on configured rules; it does not require any physical setup.
Software firewalls are installed locally on the device or devices you are trying to protect. You have much more granular control of the rules set up for each specific device running the software. Traffic can be analyzed down to the content and blocked based on keywords contained therein.
Since the software firewall is local, it is typically efficient with security alerts. Whether managing rules or users, administrators can refer to logs or notifications to determine what is happening on the devices. Knowing what is taking place on your systems at a moment’s notice works in your favor.
However, for software firewalls to work, the software would need to be installed on each device in your network. If there is no hardware firewall between the Internet and your system, your infrastructure could be susceptible to attacks.
It is also essential to ensure compatibility between your operating system and the software you wish to use. No matter how good the software is, compatibility issues weaken the effectiveness of your security.
One small factor to note is that software firewalls can be intensive on your device’s resources. While computers and servers with more capable hardware may not notice much of a difference, those with limited resources can slow down with some software firewalls. The more lightweight the software, the better your environment will run.
What is the Difference Between a Firewall and Antivirus?
Find out the exact difference between a firewall and antivirus software:
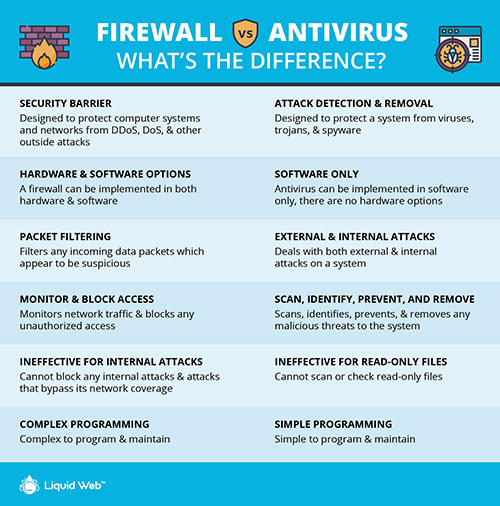
Firewall
A firewall is the state version of a router. Here, all the data packets are entering or leaving the network by passing through a firewall, and after examining them, the firewall decides whether to allow or block the packets. Traffic passes through the firewalls, and only authorized traffic is given access.
In other words, the protection is achieved by only allowing the legitimate traffic/accesses and filtering out all the unauthorized users from accessing the private network.
Antivirus
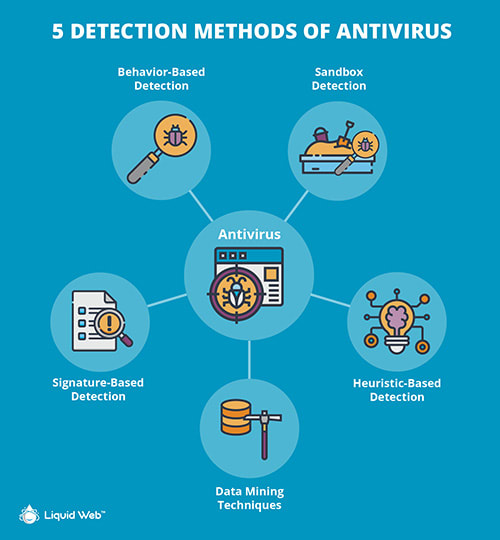
Antivirus is an application or software that provides security from malicious data coming from the Internet. Antivirus works on the three steps principle:
- Detection: First, the antivirus detects the virus from the device.
- Identification: After the detection, it identifies the type of virus or the behavior of the virus.
- Removal: After identification of the virus, it works on removal from the computer. It works as a precaution so that it removes the virus and prevents any potential virus from infecting your system in the future.
What are the Advantages and Disadvantages of a Firewall?
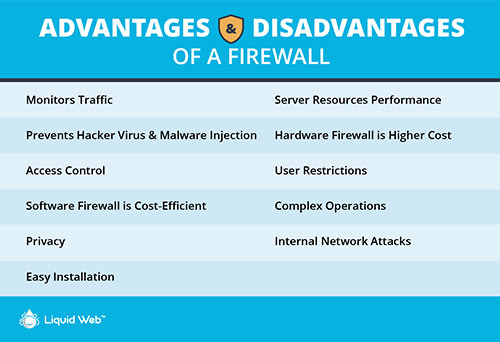
What are the Advantages of a Firewall?
As we have already discussed, the firewall is a barrier that prevents hackers from attacking a network. It will help to protect your network from suspicious activity such as malware, unauthorized traffic, and much more.
Monitors Traffic
The firewall monitors the traffic passing through it and checks if there is any dangerous malware or code attached to the packet. If any malicious packets are found, it immediately blocks them.
Prevents Hacker Virus and Malware Injection
The firewall helps to protect the server from hackers injecting viruses and malware. It does this by blocking unsolicited and unwanted incoming network traffic. In addition, a firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.
Access Control
A firewall is built with an access policy that can be executed for certain hosts and services. To prevent exploitation by hackers, it is best to block such hosts from accessing the device.
Software Firewall is Cost-Efficient
A software firewall is cheaper and comes with the latest features and updated operating systems. There are even some software firewalls that come with premium antivirus software that will provide more protection. Hardware firewalls tend to be a bit more expensive than software firewalls.
Privacy
When it comes to Internet access, privacy is one of the main concerns of a user. Hackers always look for private information. In this case, a firewall with a VPN helps to hide personal information like the domain name service (DNS) and IP address so that hackers cannot get any private details.
Easy Installation
Installing a software firewall is quite simple and does not need any professional guidance. There are tutorials available on the Internet that will help you complete the installation process. Nowadays, all modern operating systems come with pre-installed firewalls.
What are the Disadvantages of a Firewall?
Protecting and securing your business’s data is one of the most important tasks your company can undertake to prevent fraud or theft. Intrusion deterrence via firewall can be a reliable defense between your company’s network and hackers. However, a firewall should never be your company’s only line of defense.
Server Resources Performance
When it comes to performance, a software-based firewall has the capability to limit your computer’s overall performance. RAM resources and processing power are some of the factors which limit the performance. For example, the software firewall constantly running in the background uses more processing power and RAM resources, which hinders the system performance.
However, a hardware firewall doesn’t cause any system performance issues as it is a separate device entirely.
Hardware Firewall is Higher Cost
As discussed, a software firewall is cheaper and comes with the latest operating system. There is a myriad of offerings to choose from ranging in price. Usually, the hardware for a firewall will start somewhere in the $700 range for a tiny business and can quickly get into the $10,000 range. However, most companies with 15 to 100 users can expect the firewall’s hardware to cost between $1,500 and $4,000.
Purchasing, installing, and maintaining a hardware firewall is more complicated and costly than a software firewall and will require expert advice from a managed host such as Liquid Web.
User Restrictions
We know that a firewall prevents unauthorized access to our system from the network. However, this can be a problem for large organizations. The policies used by the firewall can be inflexible, preventing employees from performing certain operations. Sometimes, this can lead to security problems since the data passed through a backdoor exploit (a type of malware that invalidates normal authentication procedures to access a system) is not examined properly.
As a result, remote access is allowed to resources within an application such as files, servers, and databases. It provides the ability to remotely issue system commands and update malware.
Complex Operations
Firewalls for a large organization require a different set of staff (a dedicated security team only to maintain the firewall) for operating and maintaining them. This team will monitor and ensure that the firewall is safe enough to protect the network from violators.
What are the Types of Firewalls?
There are six different types of firewalls:
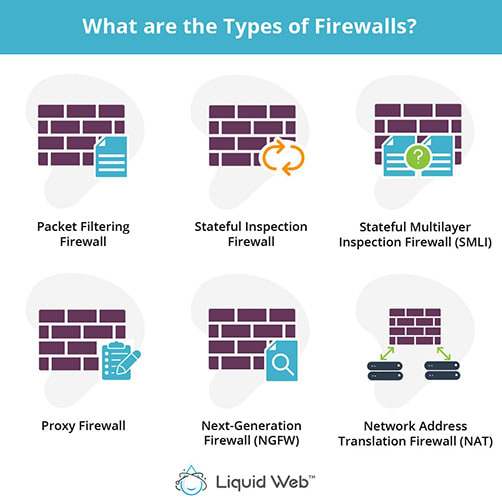
1. Packet Filtering Firewall
Packet Filtering is a specific method for implementing a firewall to monitor network connectivity. Data packets are analyzed and compared against the configuration rules or “access-list.” The firewall then determines what is allowed or denied access to your environment.
2. Stateful Inspection Firewall
Stateful Inspection techniques allow the analysis of traffic flow patterns according to state, port, and protocol. The firewall monitors activity on a connection from open to close. Next, the firewall keeps track of known, trusted packets to discern authorized data from the website or app versus any data from unauthorized sources.
3. Stateful Multilayer Inspection Firewalls (SMLI)
Stateful Multilayer Inspection Firewalls filter data packets at the network, transport, and application layers. SMLI firewalls examine entire data packets and compare them against trusted ones. These types of firewalls only allow data packets to pass if they pass the filters at each layer individually, ensuring all communication takes place with trusted sources.
4. Proxy Firewall
Proxy-based firewalls take stateful inspection a step further, preventing direct network connections between Internet traffic and the server. The firewall acts as an intermediary between your server and end-user requests. Entire packets are examined and either blocked or allowed based on set rules.
5. Next-Generation Firewalls (NGFW)
While traditional firewalls only inspect packet headers, Next-Generation Firewalls combine conventional firewall technology with additional functionality. Like SMLI firewalls, Next-Gen Firewalls analyze data within the packets to identify and stop malicious data more effectively. An NGFW includes additional functionality such as:
- Encrypted traffic verification.
- Intrusion prevention.
- Antivirus.
- Website filtering.
- Intrusion prevention.
- Deep packet inspection (DPI).
6. Network Address Translation Firewalls (NAT)
NAT firewalls are similar to Proxy firewalls, acting as intermediaries between a group of computers and outside traffic. They act as private networks, allowing multiple devices with independent network addresses to connect to the Internet with a single IP address. Devices behind this firewall remain hidden, and unsolicited communication is blocked.
Do You Need a Firewall to Keep Your Data Secure?
Yes, a firewall is as essential to security as an antivirus program. Firewalls stop malware from spreading and circulating to a network and protect against hackers attempting to penetrate a targeted system.
Disabling a firewall can:
- Cause malware injection and leave a business vulnerable to abuse, allowing viruses to infect interconnected devices and cybercriminals to execute malicious code remotely.
- Allow all data packets to enter and exit the network unrestricted. This includes expected traffic and malicious data, thereby putting the network at risk.
- Affect all devices that connect to the network.
It’s not just the associated computer that’s in harm’s way, either. Worms, a type of malware, can spread across a network connection, infecting all of the computers attached to the local area network (LAN).
What are Some Firewall Use Cases?
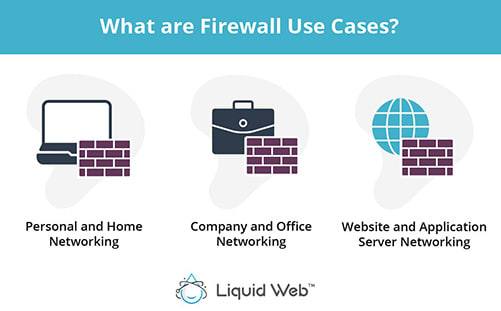
Personal and Home Networking
People that work or play from their home Internet connection most certainly need a firewall. In most cases, some firewall form gets used in most operating systems, home network routers, and antivirus software. Unless there is a need beyond these standard methods, not much else is necessary besides a firewall. You can certainly consult with your Internet Service Provider or an Information Technology professional for assistance with home networking.
Company and Office Networking
Your office or place of business needs security outside of the basics. Whether your infrastructure is set up in-house or hosted with a provider, ensuring data to and from your servers is legitimate and protected is a necessity. It is worthwhile to explore solutions for protecting your data and your servers.
Website and Application Server Networking
Hosting sites and applications with a managed provider still warrants a secure environment. DoS attacks, malware, and other exploits to software vulnerabilities are just a few things hackers deploy. With the proper configuration and rules in place, you can lock down your websites and applications from those out to get your data.
How to Install a Firewall
Here’s how to install a firewall in six steps:
1. Secure Your Firewall
Administrator access to your firewall should be limited to only those you trust. To keep out any potential attackers, make sure your firewall is secured by at least one of the below configuration actions:
- Update your firewall to the latest vendor-recommended firmware.
- Delete, disable, or rename any default user accounts, and change all default passwords. Make sure that you’re using strong passwords.
- If multiple people manage the firewall, create additional accounts with limited privileges based on responsibilities. Do not share user accounts. Track the changes and note who made what changes and why.
- Limit the subnet of IPs from which firewall configuration changes can be made.
2. Architect Firewall Zones and IP Addresses
To protect your network’s data, you should first recognize the type of data. Next, create a plan where all of the data is assembled according to the business and application needs. Structure your plan around data sensitivity level, function, and networks (or zones).
Typically, all servers that provide web-based services (email, VPN, etc.) should be organized into a dedicated zone that limits inbound traffic from the Internet. This zone is often called a demilitarized zone (DMZ). Accordingly, servers not accessed directly from the Internet should be placed under internal server zones. These zones usually contain workstations, database servers, and any point of sale (POS) or voice over internet protocol (VoIP) devices.
If you are using IP version 4, internal IP addresses should be used for all of your internal networks. The network address translation (NAT) must be configured to allow internal devices to communicate on the Internet when it’s essential (e.g., connecting modem, cable, etc.).
Once you have developed your network zone system and established the corresponding IP address strategy, you are prepared to create your firewall zones and assign them to your firewall interfaces.
3. Configure Access Control Lists
Once the network zones are specified and assigned to interfaces, you will develop firewall rules called access control lists (ACLs). ACLs determine which traffic needs the authorization to flow in and out of each zone. Your ACLs should be made as specific as possible.
To filter out unauthorized traffic, create a deny-all rule at the end of every ACL. Next, use both inbound and outbound ACLs (access control list) for each interface. If possible, disable your firewall administration interfaces from public access. Remember to be as detailed as possible in this phase.
Make sure to look into the firewall’s ability to control next-generation level flows:
- Can it block traffic based on web categories?
- Can you turn on advanced scanning of files?
- Does it contain some level of intrusion prevention system (IPS) functionality?
4. Configure Your Other Firewall Services and Logging
If preferred, the firewall should work as a network time protocol (NTP) server, dynamic host configuration protocol (DHCP) server, intrusion prevention system, etc. Disable any services you don’t plan to use.
5. Test Your Firewall Configuration
Verify that your firewall is blocking traffic that should be blocked according to your ACL configurations. This should include both penetration testing and vulnerability scanning. Ensure that you’re keeping a secure backup of all firewall configurations in case of any failures.
If everything checks out, your firewall is ready for production. Before making any changes, test the process of reverting back to a configuration, make a note, and test your recovery procedure.
6. Firewall Management
Once your firewall is configured and running correctly, you will need to maintain it to function optimally. Make sure to update firmware, perform vulnerability scans, monitor logs, and review your configuration rules at least every six months.
How to Install a Software Firewall
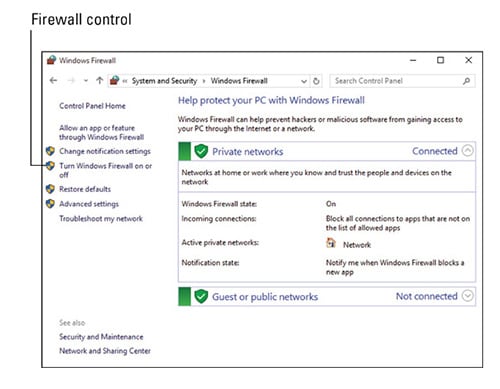
Windows comes with a firewall called Windows Firewall. It’s accessed from the Control Panel. Please follow these steps to ensure the firewall is turned on:
- Open the Control Panel.
- Click on the System and Security heading.
- Click on Windows Firewall heading.
- Click the Turn Windows Firewall On or Off link on the left side of the Windows Firewall window.
The firewall has now been turned on.
Get Secure with a Liquid Web Hardware Firewall
Liquid Web is a proud Cisco shop and stocks several versions of its hardware firewall devices. These devices are also powerful enough to handle traffic from multiple servers, including dedicated servers. We also employ a full staff of dedicated networking professionals 24/7/365 who can manage and maintain your fully-managed networking infrastructure. Get started with a hardware firewall today.

